Introducing Luna, Combining the Power of Splunk and Slack!



Data visualizations in Splunk are an extremely powerful way to analyze and derive value from the mountains of data collected every day. Today, I’d like to cover how to create a custom visualization in Splunk using the C3.js library, which is built on top of the extremely popular and powerful D3.js data visualization library. One of the advantages of using C3 is that the syntax is somewhat simpler to use than D3. While “D3” stands for “Data-drive Documents,” “C3” stands for “Comfortable,...

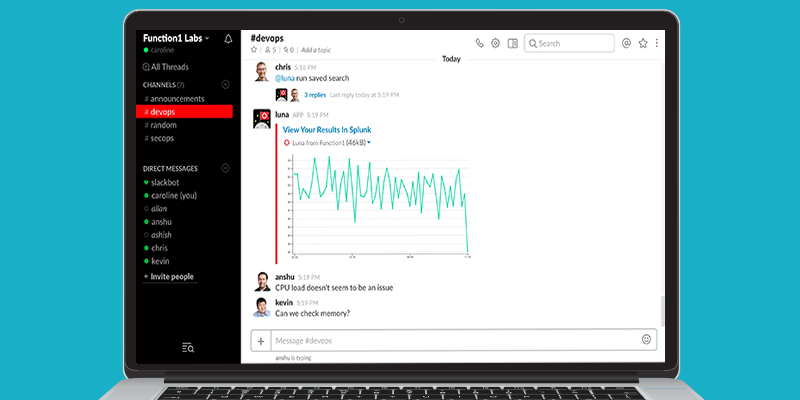
We're excited to announce the release of our new Slack App for Splunk! The Slack App for Splunk helps to gain insight into your company’s Slack environment.
The app seamlessly monitors your team's Slack activity by leveraging the Slack App for Splunk’s modular inputs. The messages generated in your public Slack channels are collected and indexed into Splunk, ready for reporting!
The Slack App for Splunk also provides prebuilt dashboards for Slack monitoring. The app effortlessly track metrics including: where and how often your users are logging in and what channels are being...

One of the longest-standing and most common challenges to both information security and web development teams is the brute force attack. Although this form of attack has been around for many years, it is still one of the most popular and widely used password-cracking methods. In terms of impact, brute force attacks are a very serious threat capable of affecting millions of accounts. If these attacks are not detected and addressed in a timely manner they can lead to theft of intellectual property and personally identifiable information, significant financial losses,...

Recently, I fixed a malfunctioning email from Splunk. It included a PDF of a dashboard, “a scheduled PDF.” The dashboard wasn’t documented...


It comes as no surprise that as the banking industry is increasing its online presence, financial organizations are making fraud detection and prevention a top priority. Fraud can have a significant impact to organizations both financially and operationally. Of course, in addition to large monetary losses, damage to reputation and customer relations can also occur that further highlight the impact of fraud.
The ability for organizations to perform advanced analytics on their data is necessary to recognize and respond to patterns of fraud. Simply stated, quicker...

Encryption of some fields when creating a modular input is sometimes needed when security becomes an issue. There are a few ways with the most common being the creation of a setup.xml file for the modular input schema. When using setup.xml however, you lose some of the modular input schemas built in to the python SDK. However, when not using setup.xml and still would like to use the python SDK to encrypt an input field it is still possible with a bit of work. In this writing I will go over one way of encrypting an input field using an additional field as an identifier.
To start off...
