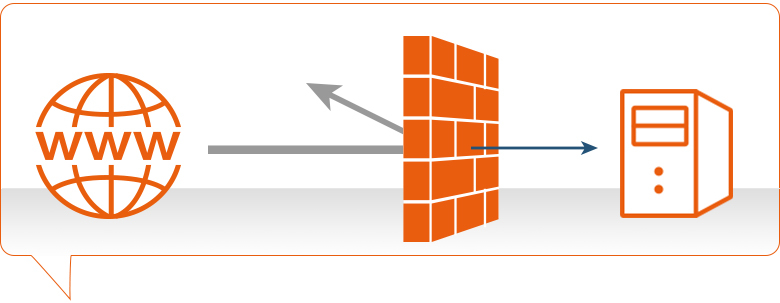
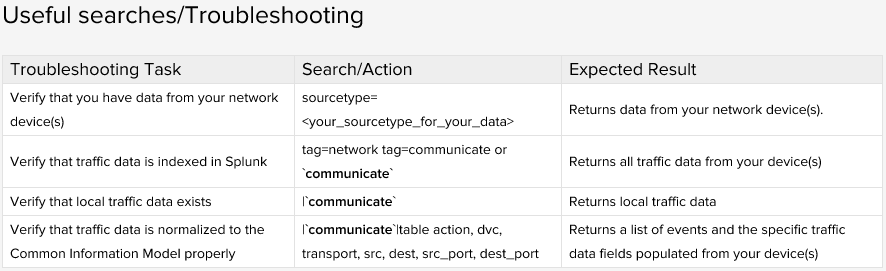
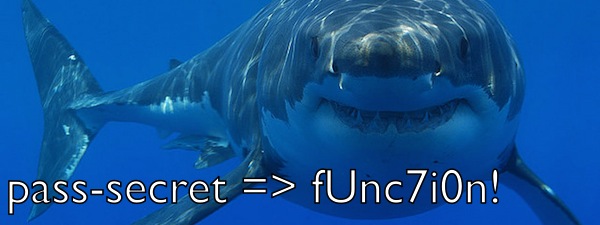
After a record-breaking Cyber Monday (with online sales soaring to $6.59 billion - a 16.8% increase over last year), Adobe is predicting that this will be the first-ever holiday season to surpass $100 billion in online sales. This is clearly fantastic news if you're in e-...
5 Tips to Keep Your Customers Safe this Holiday Season