Splunking Microsoft Windows Firewalls
Intro
Without exception, if you are an experienced security analyst, then you know the importance of firewall logs and the invaluable network traffic related data that they provide. Many of the key strategies of information security revolve around the network traffic of an organization and the rules that govern it. No matter the type of firewall, whether it is a hardware appliance or a software/OS level firewall, it should be logged for security and auditing purposes.
Given the significance of the firewall logs themselves, it is easy to see the importance of monitoring for configuration changes to firewalls. If an ill-intentioned person were to modify the configuration of a firewall, they could easily introduce security weaknesses into a network.
In today’s blog we will explore a method designed to provide robust auditing and logging of modifications to Windows Firewalls.
Requirements
The information and instructions provided here pertain to Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2.
Implementation
Windows Firewall Audit Settings
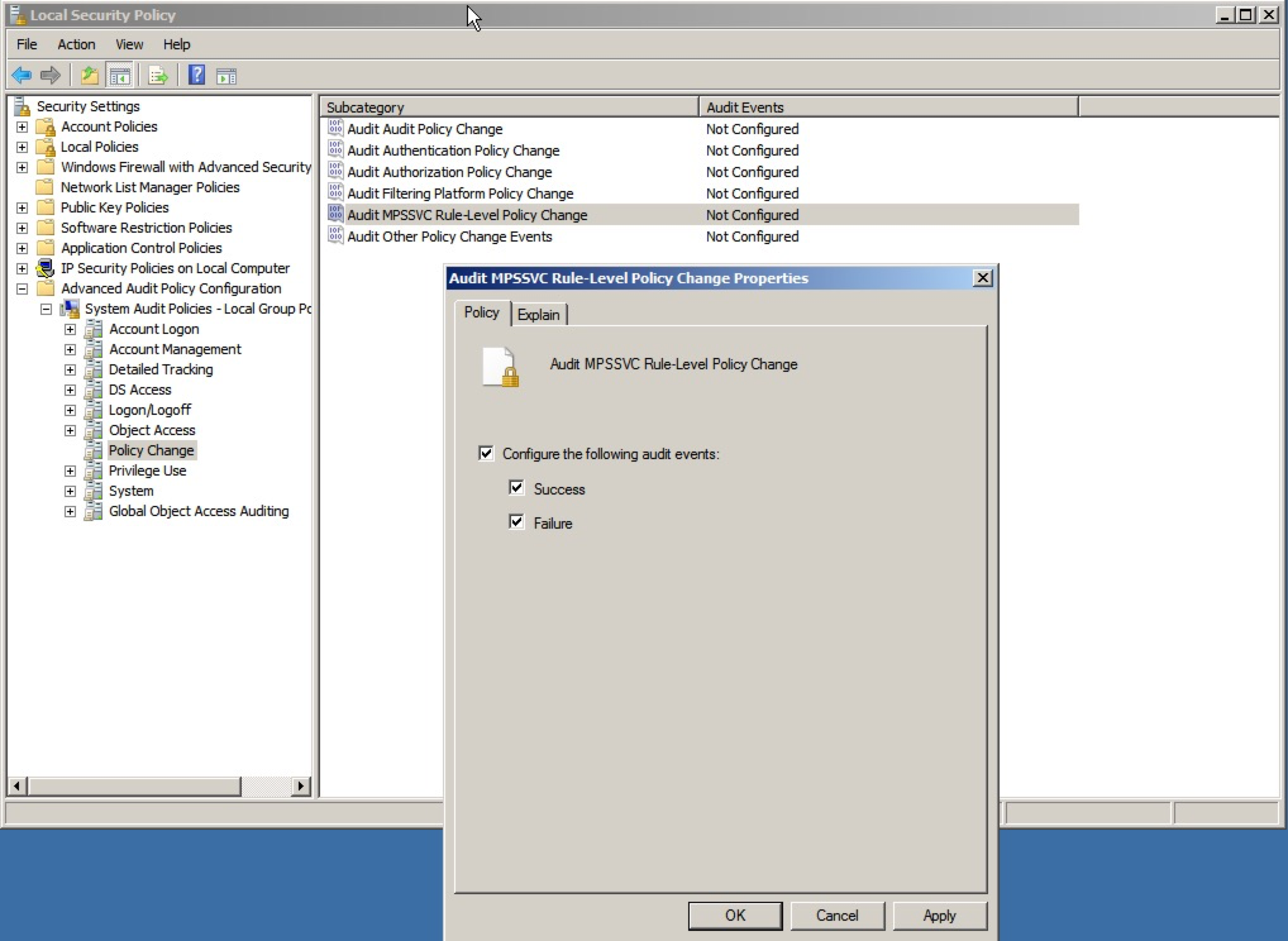
In order to ensure proper logging of all relevant modifications to the Windows Firewall, certain audit policy settings need to be enabled. Like all other audit settings, they can be enabled via updates pushed out through a GPO (Group Policy Object) or locally via edits to the Local Security Policy.
The location within Local Security Policy for these specific audit settings is as follows (see screenshot):
Security Settings: Advanced Audit Policy Configuration
Category: Policy Change
- MPSSVC Rule-Level Policy Change
- Filtering Platform Policy Change
Modification to the Splunk Add-on for Microsoft Windows
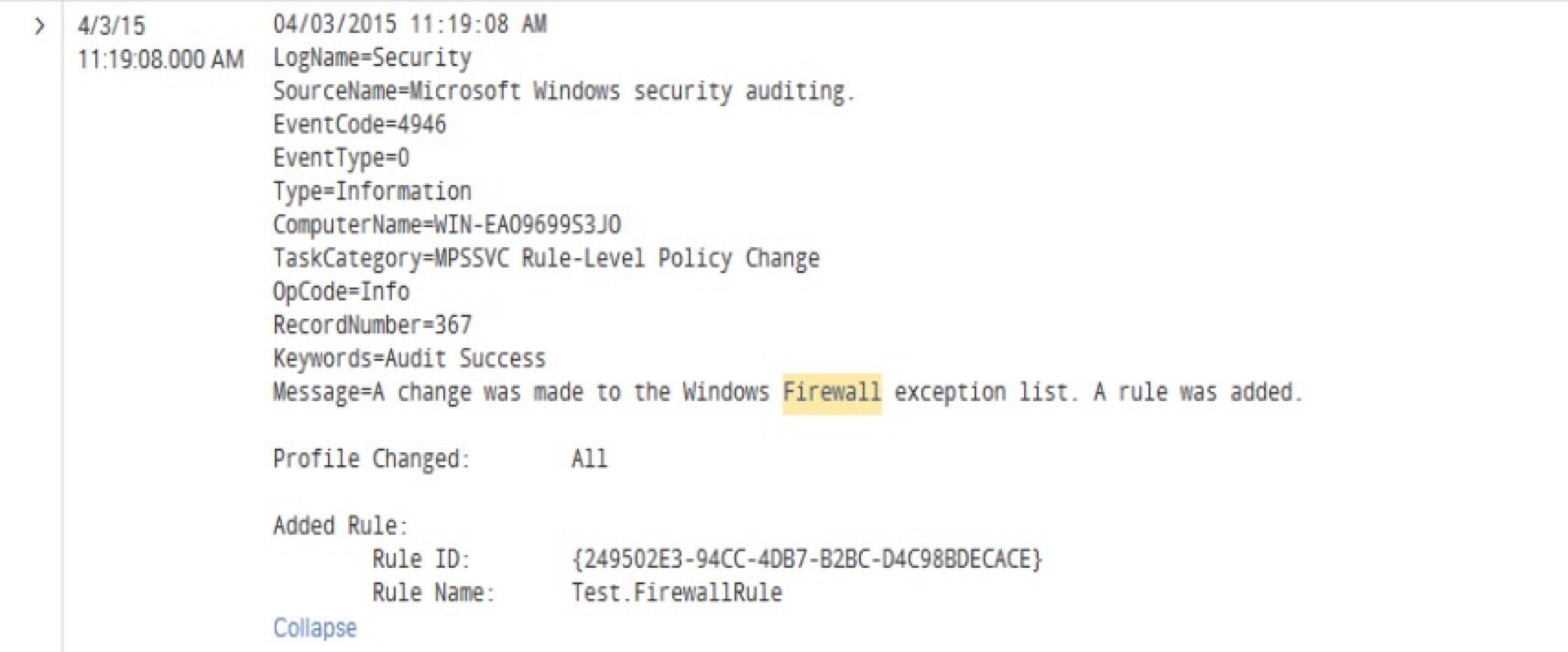
Once you have enabled the audit settings on your Windows server, the next step is to enable logging of these new events within Splunk. By default, Windows will now start recording firewall modifications within WinEventLog:Security (security.evtx). Assuming that you have the Splunk Add-on for Microsoft Windows installed on your servers and have the WinEventLog:Security input enabled, then you will start receiving some of these related without any further configuration. While this is a good start, the events that are generated here do not provide as much detail as those that are recorded within the Windows Firewall With Advanced Security log.
Here is an example event where I added a new firewall rule. When the event is sent to Splunk via the standard WinEventLog:Security log it looks like this (see screenshot):
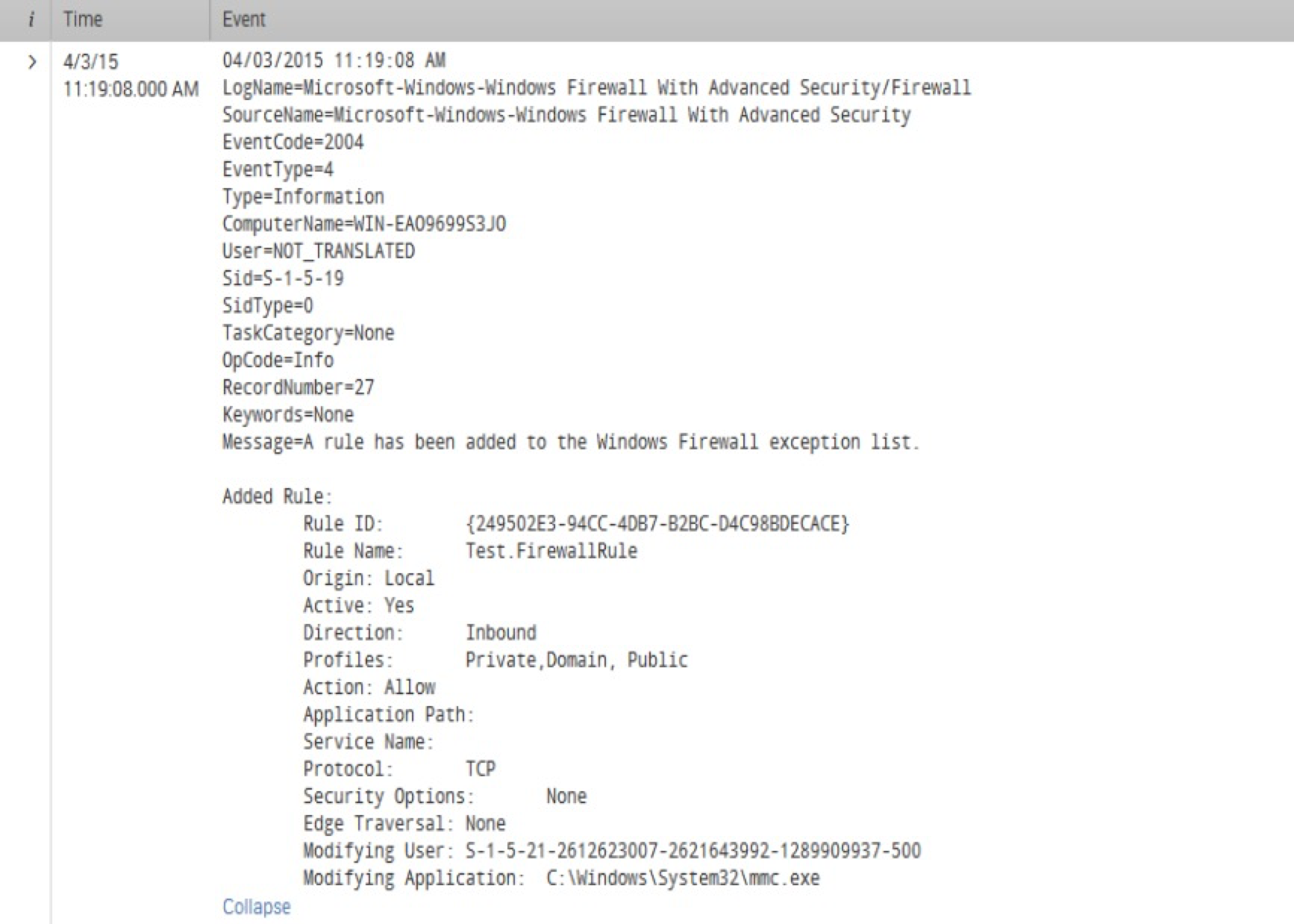
Here is the same event in the Windows Firewall With Advanced Security log (see screenshot):
As you can see, the second event provides much more detail regarding the specific firewall rule that was added to the server. These additional details can be of great help for more advanced reporting and alerting within Splunk and the Enterprise Security app.
Here are the modifications to inputs.conf within Splunk_TA_windows that are required to capture the firewall log. Of course feel free to modify the settings as needed for your environment.
[WinEventLog://Microsoft-Windows-Windows Firewall With Advanced Security/Firewall]
disabled = 0
start_from = oldest
current_only = 0
checkpointInterval = 5
index = windows
What's Next?
Once you have the firewall events in Splunk, take some time to examine the automatically extracted fields. With this data you should have no problem moving forward building useful dashboards, reports and alerts.
From personal experience, I found it very useful to map these events to the Change Analysis data model. I chose to utilize the Endpoint Changes sub-node of the data model. From there I was able to build custom searches against the accelerated data and save them as correlation searches within the Splunk App for Enterprise Security. As a result, now I see a notable event generated within ES for every modification to a Windows Firewall within the network.
Thanks for reading and please leave a comment or email us at info@function1.com with any questions. Happy Splunking!
- Log in to post comments