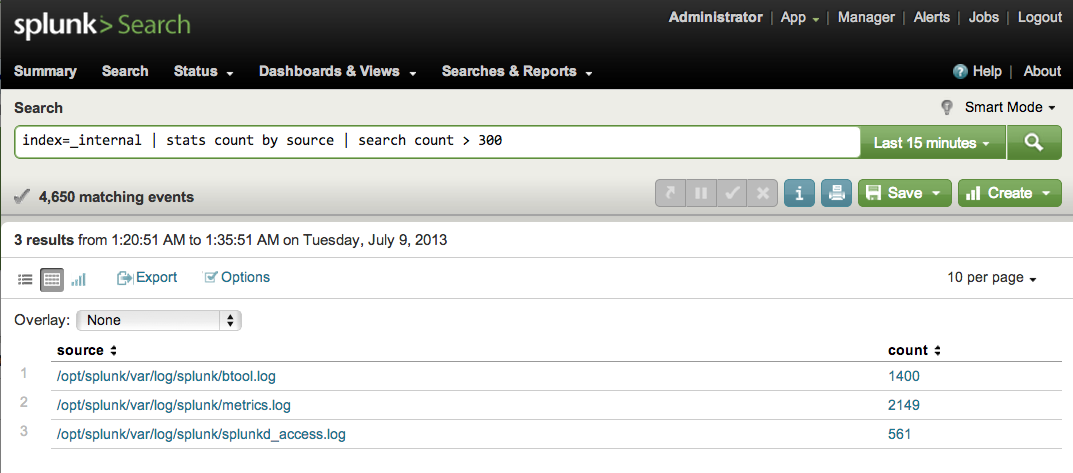
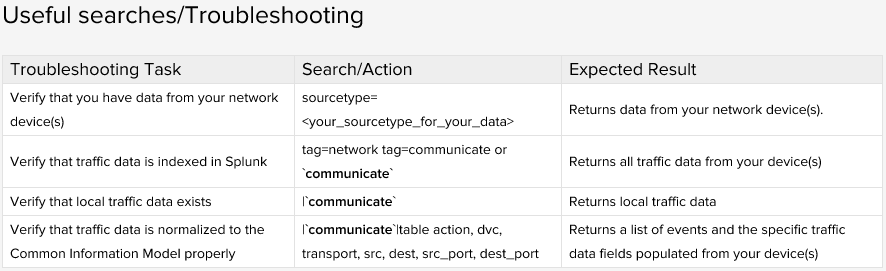
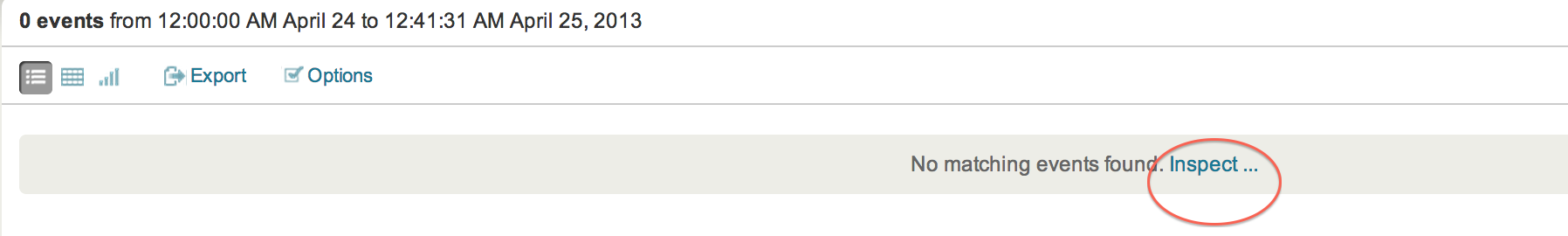
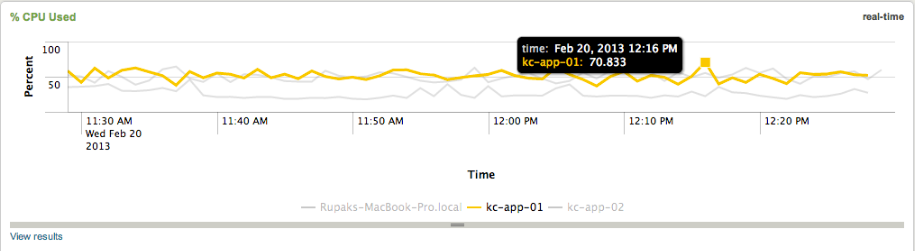
You have a working Splunk environment, and decide to utilize the deployment server functionality to make the deployment of apps and management of configuration files easier.
You start by setting up the serverclass.conf file for the forwarder as the following:
[global] continueMatching = true whitelist.0 = * restartSplunkd = false [serverClass:forwarder_serverclass] whitelist.0 = *spkfwd* [serverClass:forwarder_serverclass:app:forwarder_inputs] [serverClass:forwarder_serverclass:app:forwarder_outputs]
Next, you set up the deploymentclient.conf on the...