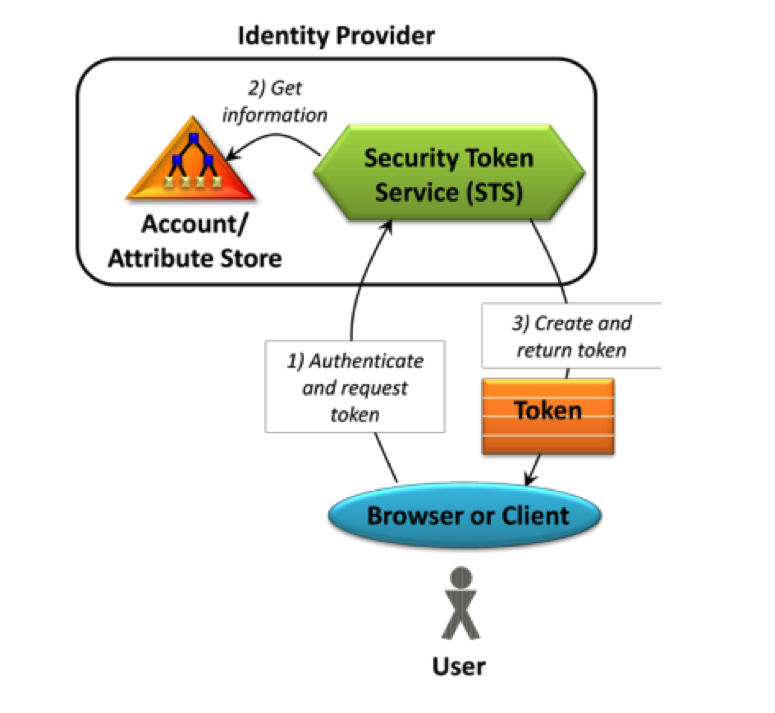
Imagine a world where you don’t have to worry about handling authentication for different types of users of your application. In modern day information technology, businesses want to interoperate with other businesses, and government organizations want to provide more integrated services to citizens. However, different systems use different authentication systems and businesses want to integrate in a secure, legally compliant manner.
Given this environment where user accounts and applications are located in completely different networks or organizations, imagine that every request...